Introduction to Exchange 2019 Security Updates
Microsoft Exchange 2019 received security updates in November 2024 as announced by the Exchange Team, however the release was quickly pulled due to Exchange Services not wanting to start etc.
I noticed that in my environment, the POP/IMAP services would not start and on some servers the Active Directory Service would not start. This update affected transport rules in Exchange Server.
Details of the November 2024 Security Update (v1)
The November 2024 Security Update for Exchange 2019, referred to as v1 since v2 was released to addresses issues that arose. This update did include a few items such as:
- Improvements in Exchange Server AMSI integration
- Non-compliant RFC 5322 P2 FROM header detection
- ECC certificate support improvements
For a deeper understanding of each improvement or update, you can refer to the link below:
https://techcommunity.microsoft.com/blog/exchange/released-november-2024-exchange-server-security-updates/4293125Introduction to Security Update v2
Microsoft fixed the issue and released v2 of the November 2024 Security Update that should be applied and you can view the reasons in the next section. Here is a link to the Exchange Team Blog outlining everything:
https://techcommunity.microsoft.com/blog/exchange/re-release-of-november-2024-exchange-server-security-update-packages/4341892Reasons to Upgrade from v1 to v2
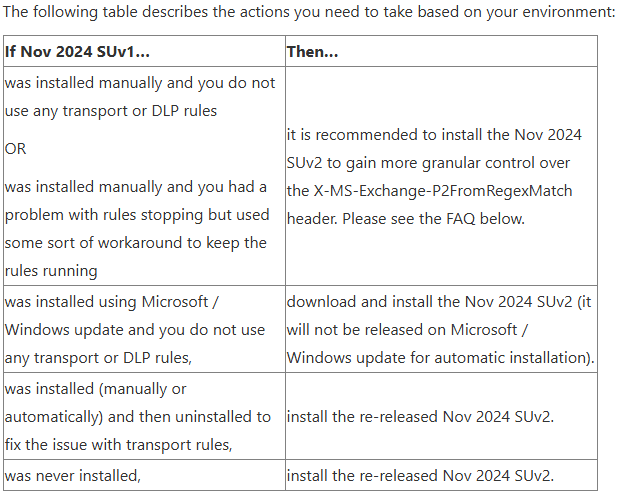
If you did apply the November SUv1 update to your Exchange 2019 servers, be sure to update to v2, here is a list of reasons provided by the Exchange Team.
Take note that this update will not be released to Windows Updates. The link above has all the info.
Installation Process of the November 2024 SUv2 Update for Exchange Server 2019
The installation is the same as any other update. You need to launch an elevated command prompt, navigate to the download directory for the Security Update and then run the MSI.
Conclusion and Future Outlook
Upgrading to any security update is advised as you will not only be on the latest patches, but also close any security holes that were identified and fixed in the update.
If you do have a lab, you should test it before rolling out the update to your production servers, if you do not have a lab, feel free to reach out to me, I also test new updates as I have various labs on different versions and scenarios and can give you insight as to what I see or if any issues were encountered.
The v1 update did get pushed automatically in my environment and it broke a few servers but I was able to fix it and then apply v2.
Hope it helps.
