Many admins save credentials in text, log, and other format files on servers, this can be a once off thing where they are troubleshooting something or they saved it there, thinking it is in a safe place and because nobody has access to servers generally, only themselves and other admins.
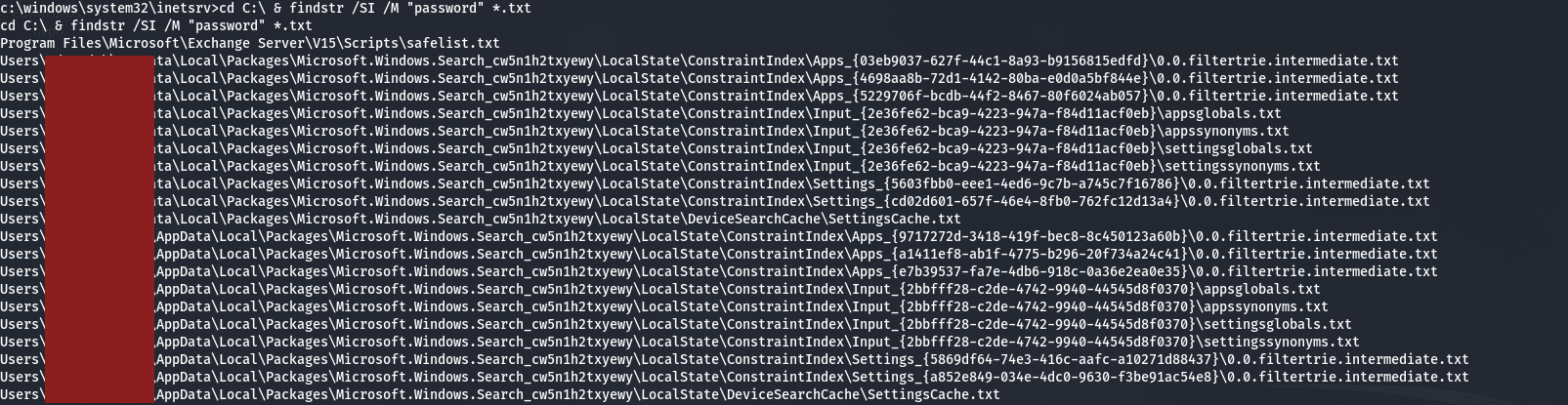
Attackers are always looking for interesting files. In this example, I have gained SYSTEM access to the Exchange Server and I ran a command to search for the word “password” in Text files. Here is the command used:
cd C:\ & findstr /SI /M "password" *.txtYou can add other extensions to the end such as *.log or *.db or change the word.
Below is the output of the search:
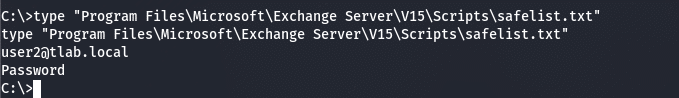
I had a friend of mine create a text file with dummy credentials and save it to a location. After going through each file, I found the credentials that he thought was in a safe place. After using the “type” command to read the text file, bingo, I now have another account I can enumerate and escalate (The account is fictitious, just used for demo purposes):
Conclusion
As you can see, storing credentials in plain text on a server or workstation is not safe. This file may have contained a “Domain Admins” account details or a “SQL Database” Administrator account details.
Hope it helps
