In one of my previous posts, we looked at Cipher Suites and locking down Server 2016 with Exchange 2016.
In my lab, I ran the same software but this time on Server 2019 running Exchange 2019.
On Server 2016 almost all the protocols were selected along with the ciphers, hashes and key exchanges.
In Server 2019, it is pretty tight except for the fact that you have Diffie-Hellman Key Exchange enabled, below are the Schannel settings:
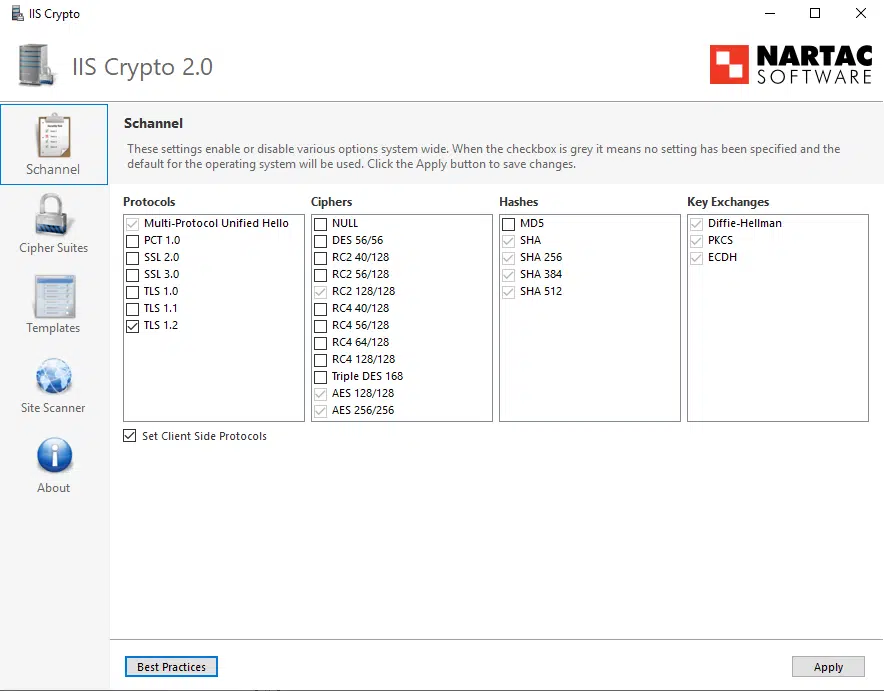
Now if we look at the actual Cipher Suites, it has a whole lot less in it, compared to Server 2012 R2 and Server 2016:
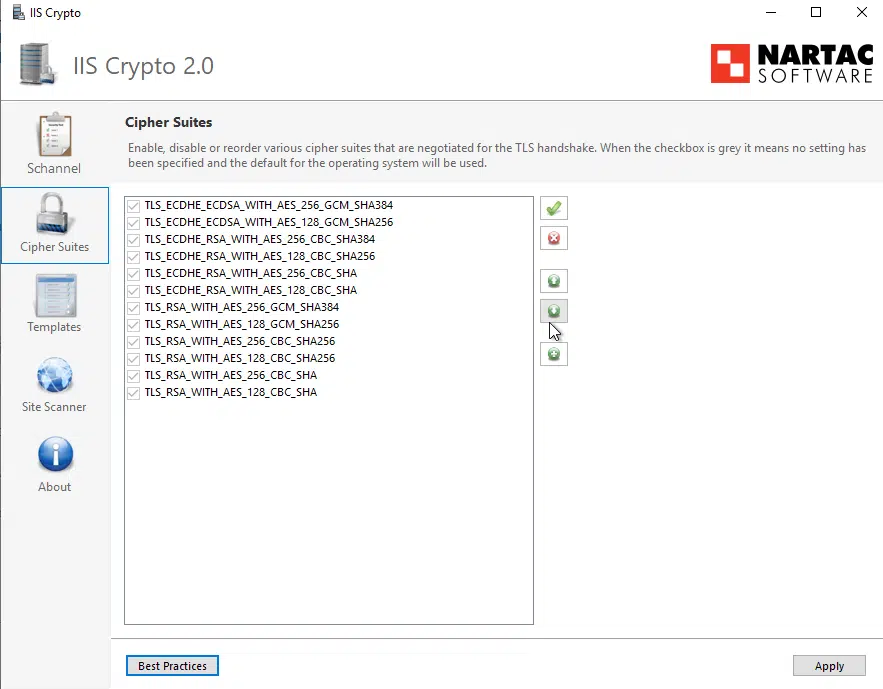
The server lockdown is good, I removed the Diffie-Hellman Key Exchange and rebooted the server, no issue with Exchange 2019.
Hope it helps.
