Over the past few years, Microsoft Exchange Server has come under heavy attack and with each new Cumulative Update (CU) and Security Update (SU), CVE’s are addressed and closed.
The problem comes in when organisations do not patch servers (as mentioned in a few of my other blog posts) and say, you cannot reach my Exchange Server from the internet or we use it internally so no need to patch something that ain’t broken.
Yes if the servers are not exposed then maybe you have mitigated the risk externally a bit but what about a bad actor that has access to your internal network? Gives them a nice playground of ways to extort data from email and demand ransomware payouts.
I put my lab Exchange Server behind a firewall in my lab and only exposed the Exchange ports to the internet. Running tools like Shodan.io, it revealed the Exchange ports and SSL certificate and lots of other information. NMAP scan also reveals the Exchange ports plus others that I thought “were not” open to the internet.
Testing a POC (Proof of Concept) on my Lab Exchange Server.
I went searching for NMAP Scripts that can be used to check Exchange Servers, yes there are many ways to check information and came across one on GitHub that worked rather nicely.
Righel on Github has an NSE script that can be used with NMAP which you can read about and download here:
https://wwwgithub.com/righel/ms-exchange-version-nse
What this script basically does is check the Microsoft Exchange Server version with CU and/or SU and provides arguments that show what CVES are present. The CVES it picks up may not only be for Exchange but 3rd party tools as well. I took this script and ran it against my lab, this server is not fully patched with the October SU for Exchange 2016 for a reason to test exploits out. This is what was returned from the NMAP scan:
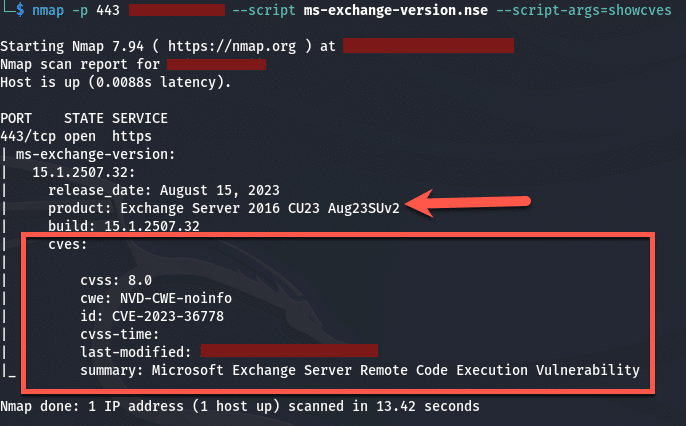
The above information means that the CVE (CVE-2023-36778) can be exploited and they will gain access to the environment.
Conclusion
As you can see with the output above, bad actors can get information about your Exchange Servers and use it to their advantage, can be Exchange Servers with loads of mailboxes or a few or that do not have mailboxes on but is just used for Hybrid and they can exploit the CVE’s highlighted and gain access to your environment. Given the fact that ransomware is on the rise, make sure that Exchange Servers are patched.
If bad actors gain access, they will look for other applications that are not patched and exploit that as well which can ultimately lead to domain take over.
If you are not sure about patching, you can reach out to me and I will gladly guide you.
Hope it helps.
