In March 2020 when we had many Exchange servers world wide attacked, the Team at Microsoft put together a nice PowerShell script that provides plenty of output but the most important part is it gives you an overview of CVE vulnerabilities on the Exchange Server.
The PowerShell script only works with Exchange 2013, Exchange 2016 and Exchange 2019.
The link to the website is as follows:
https://wwwmicrosoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/
The GitHub page provides a lot of information and explains each section in detail. If you are running Windows Server 2019 Core, remember that you need to enter “PowerShell” at the command line and press enter before you run it.
The script takes a couple of minutes to run, if you block scripts on your server, you will need to allow it to run or the script will fail as the execution policy is restricted. Below is an example of the output, this was run on my lab server:
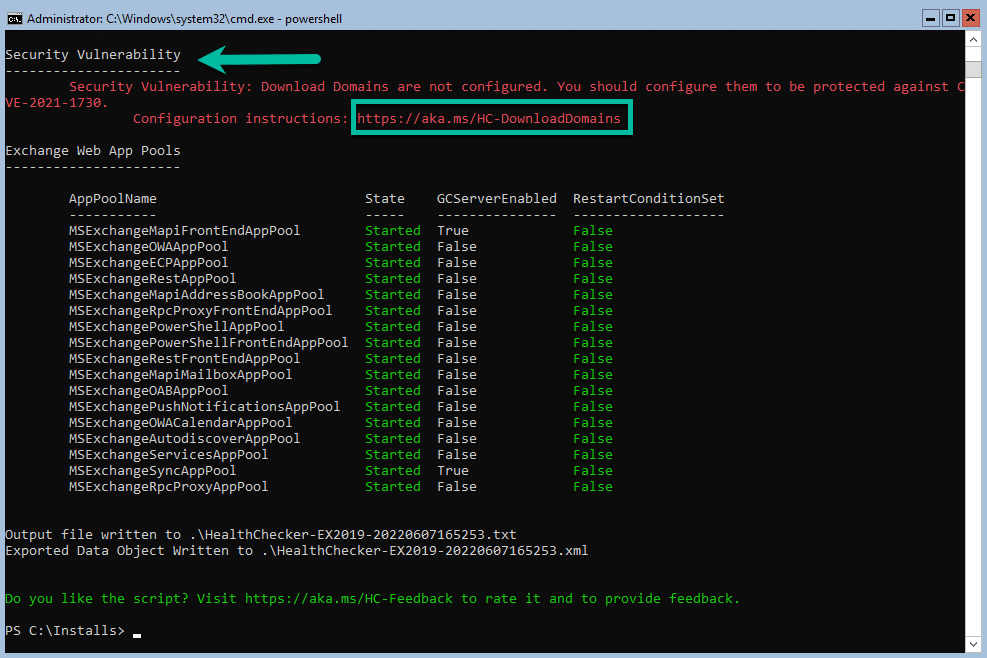
As you can see above, it picked up a Security Vulnerability on the server and it provides you with link that explains in detail how to resolve it. The PowerShell script gets updated often so ensure that you have the latest one.
One thing to take note of is and what I am doing a lot is comparing the SHA256 Hash of the PowerScript or CU from Microsoft to make sure that everything matches. You can use the CertUtil tool in windows to check the Hash to ensure you have a legitimate file.
Hope it helps.
